- January 3, 2024
- 02:44 PM
- 0

Update on 1/4/24 added below.
Orange Spain suffered an internet outage today after a hacker breached the company's RIPE account to misconfigure BGP routing and an RPKI configuration.
The routing of traffic on the internet is handled by Border Gateway Protocol (BGP), which allows organizations to associate their IP addresses with autonomous system (AS) numbers and advertise them to other routers they are connected to, known as their peers.
These BGP advertisements create a routing table that propagates to all other edge routers on the internet, allowing networks to know the best route to send traffic to a particular IP address.
However, when a rogue network announces IP ranges usually associated with another AS number, it is possible to hijack those IP ranges to redirect traffic to malicious websites or networks.
According to Cloudflare, this is possible because BGP is built on trust and the routing table will be updated based on which advertiser has the shortest and more specific route.
To prevent this, a new standard called Resource Public Key Infrastructure (RPKI) was created that acts as a cryptographic solution to BGP hijacking.
"Resource Public Key Infrastructure (RPKI) is a cryptographic method of signing records that associate a BGP route announcement with the correct originating AS number," explains a Cloudflare article on RPKI.
By enabling RPKI with a routing body such as ARIN or RIPE, a network can cryptographically certify that only routers under their control can advertise an AS number and their associated IP addresses.
Hacker breaches RIPE account to break BGP
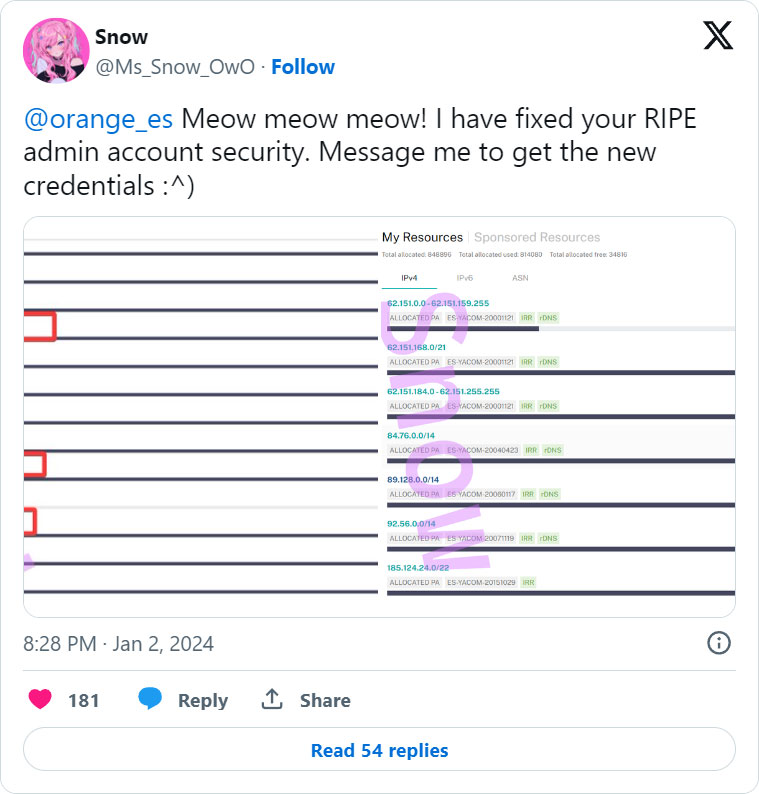
Yesterday, a threat actor named 'Snow' breached the RIPE account of Orange Spain and tweeted to Orange Spain to contact them about getting new credentials.
Since then, the attacker modified the AS number associated with the company's IP addresses, and enabled an invalid RPKI configuration on them.
Announcing the IP addresses on someone else's AS number and then enabling RPKI effectively caused these IP addresses to no longer be announced properly on the internet.
"As we see, what they did was create some ROA /12 records, which basically indicate who is the AUTHORITY over a prefix (i.e., the AS that can announce it)," Felipe Cañizares, CTO from DMNTR Network Solutions, told BleepingComputer.
"These grouped together the /22 and /24 prefixes announced by Orange Spain, indicating that the AS that should announce that prefix was AS49581 (Ferdinand Zink trading as Tube-Hosting)."
"Once this was done, they activated RPKI on that /12... and goodbye..."
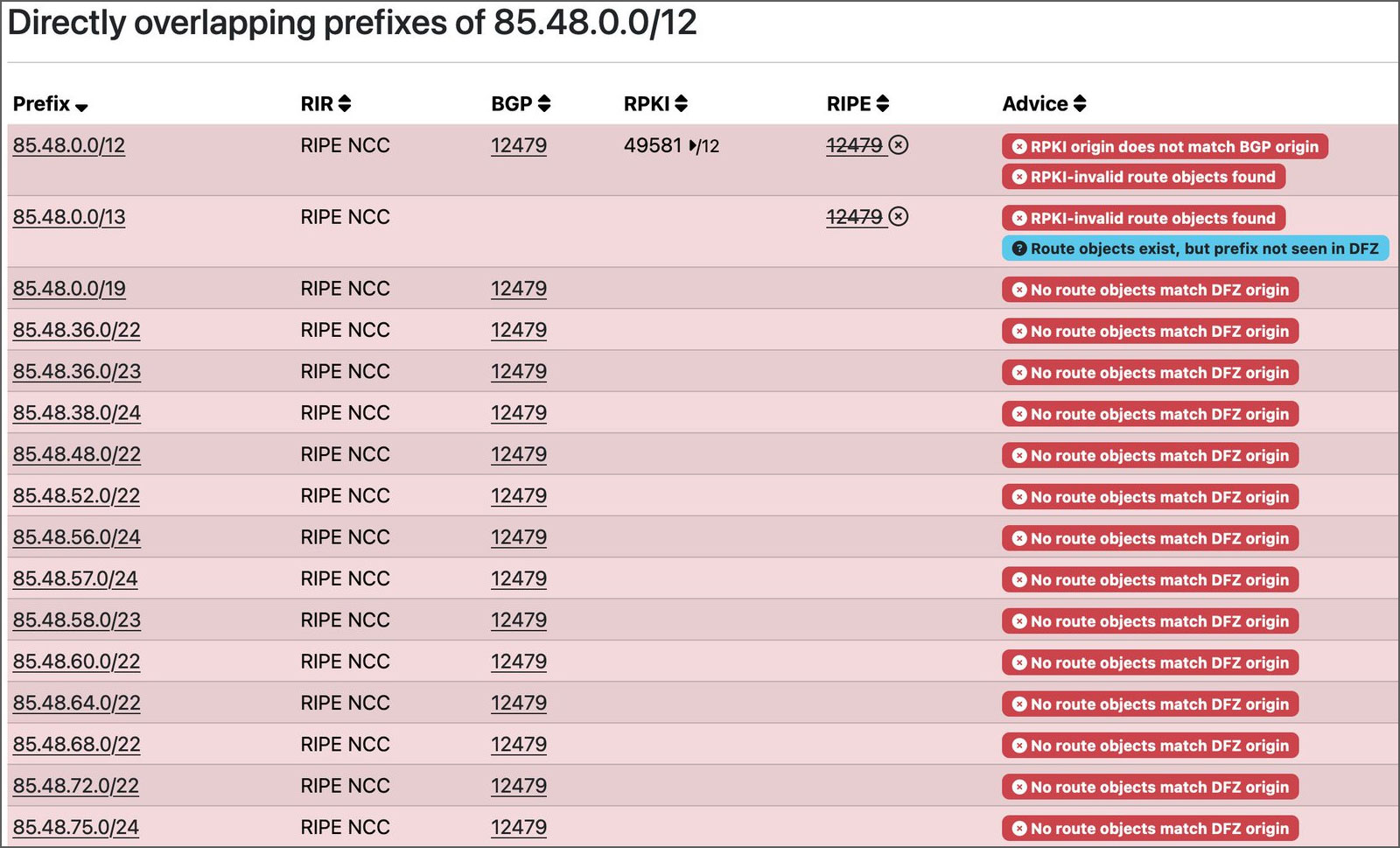
Source: Cañizares
This led to a performance issue on Orange Spain's network between 14:45 and 16:15 UTC, which can be seen in the Cloudflare traffic graph below for AS12479.
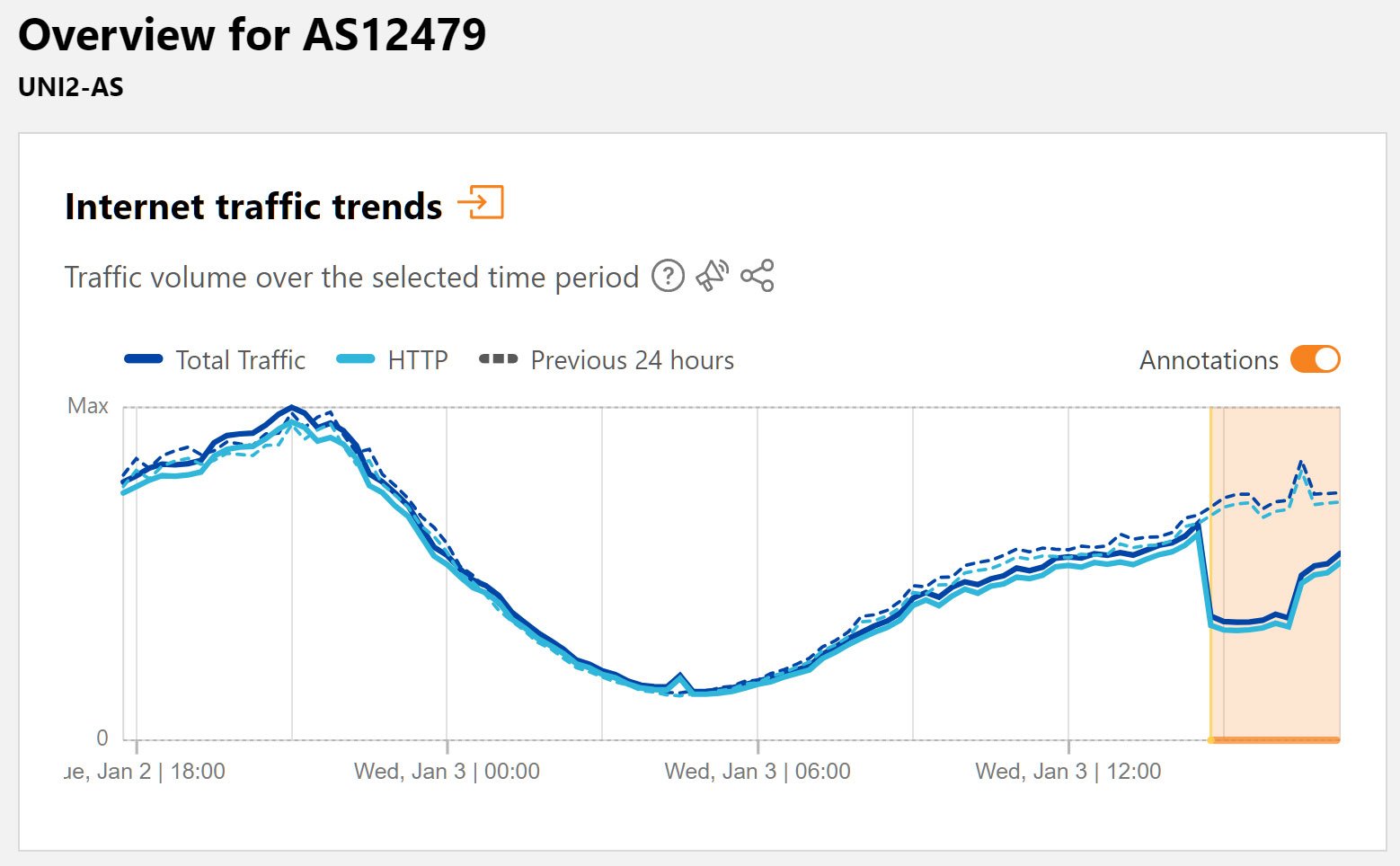
Source: Cloudflare
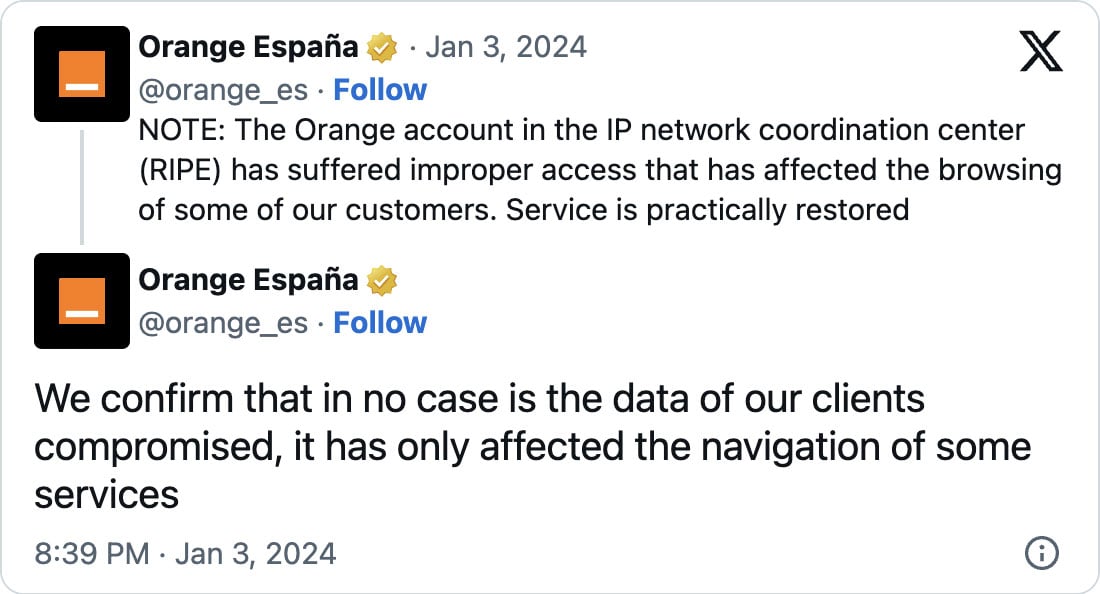
Orange Spain has since confirmed that their RIPE account was hacked and has begun to restore services.
"NOTE: The Orange account in the IP network coordination center (RIPE) has suffered improper access that has affected the browsing of some of our customers. Service is practically restored," Orange Spain tweeted.
"We confirm that in no case is the data of our clients compromised, it has only affected the navigation of some services."
It is unclear how the threat actor breached the RIPE account but Cañizares told BleepingComputer that he believes Orange Spain did not enable two-factor authentication on the account.
Cañizares has created a thread on X summarizing how this attack took place.
BleepingComputer contacted Orange Spain with questions about the attack but has not received a reply at this time.
Credentials likely stolen via malware
While Orange Spain has not disclosed how its RIPE account was breached, the threat actor provided a clue in a screenshot posted to Twitter that contained the hacked account's email address.
Alon Gal of cybersecurity intelligence service Hudson Rock told BleepingComputer that this email and an associated password for the RIPE account were found in a list of accounts stolen by information-stealing malware.
"The Orange employee had their computer infected by a Raccoon type Infostealer on September 4th 2023, and among the corporate credentials identified on the machine, the employee had specific credentials to "https://access.ripe.net" using the email address which was revealed by the threat actor ([email protected])," explains research from Hudson Rock.
According to Gal, the password for the account was 'ripeadmin,' which is a very easy password for a critical account.
The hacker, Snow, later confirmed Hudson Rock's findings, saying on Twitter that they found the account in public leaks of stolen data.
"For those wondering how i acquired access to the account in the first place, let me just say that the password security was very questionable," Snow posted on Twitter/X.
"I was just looking into public leaks of bot data and came across the ripe account with the password "ripeadmin" and no 2FA, No SE at all."
When asked why they hacked the account, the hacker says they did it for the "lulz," or in other words, for the laughs.
Information-stealing malware has become the bane of the enterprise, as threat actors use them to gather credentials for initial access to corporate networks.
Threat actors commonly purchase stolen credentials from cybercrime marketplaces, which are then used to breach networks to perform data theft, cyber espionage, and ransomware attacks.
For this reason, all accounts must have two-factor or multi-factor authentication enabled so that even if an account is stolen, attackers cannot log in to the account.