- January 21, 2024
- 11:19 AM
- 3

A widespread Facebook phishing campaign stating, "I can't believe he is gone. I'm gonna miss him so much," leads unsuspecting users to a website that steals your Facebook credentials.
This phishing attack is ongoing and widely spread on Facebook through friend's hacked accounts, as the threat actors build a massive army of stolen accounts for use in further scams on the social media platform.
As the posts come from your friends' hacked accounts, they look more convincing and trustworthy, leading many to fall for the scam.
The phishing campaign started around a year ago, with Facebook having trouble blocking the posts as they continue to this day. However, when new posts are created and reported, Facebook deactivates the Facebook.com redirect link in the post so that they no longer work.
"I can't believe he is gone" scam
The Facebook phishing posts come in two forms, with one simply stating, "I can't believe he is gone. I'm gonna miss him so much," and containing a Facebook redirect link.
The other uses the same text but shows what appears to be a BBC News video of a car accident or other crime scene, as shown below.
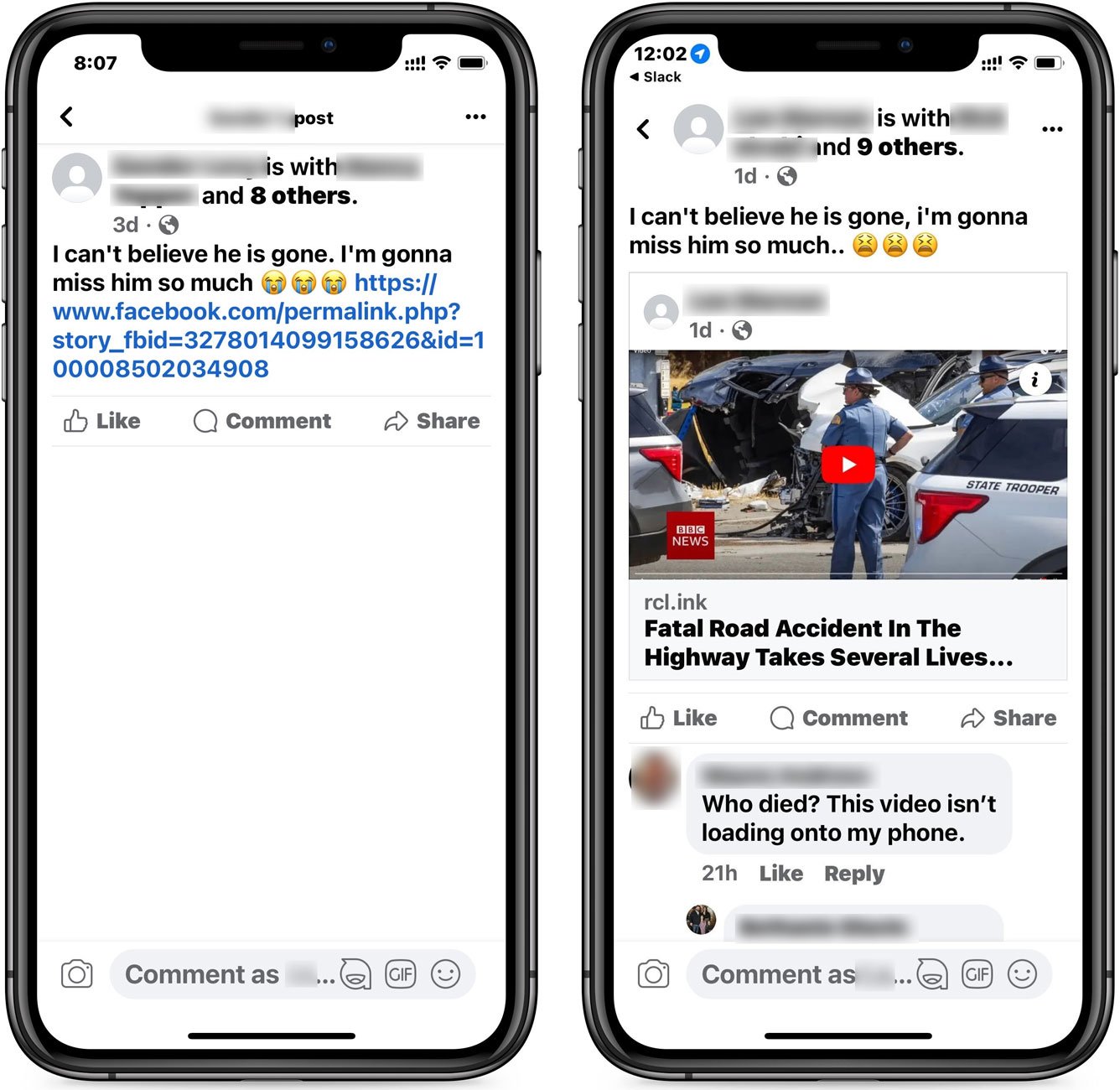
Source: BleepingComputer
When BleepingComputer tested the links in the phishing posts, they brought us to different sites depending on the type of device you are using.
Clicking on the link from the Facebook app on a mobile device will bring visitors to a fake news site called 'NewsAmericaVideos' that prompts them to enter their Facebook credentials to confirm their identity and watch the video.
To entice a visitor to enter their password, they show what appears to be a blurred-out video in the background, which is simply an image downloaded from Discord.
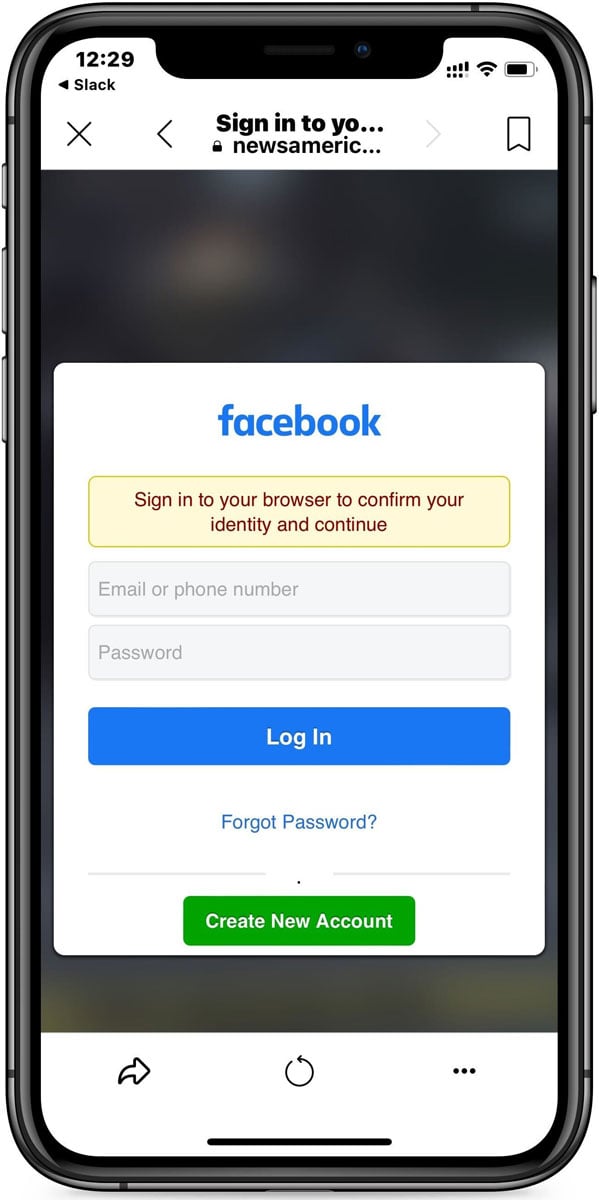
Source: BleepingComputer
If you enter your Facebook credentials, the threat actors will steal them, and the site will redirect you to Google.
While it is not known what the stolen credentials are used for, the threat actors likely use them further to promote the same phishing posts through the hacked accounts.
Visiting the phishing pages from a desktop computer causes a different behavior, with the phishing sites redirecting users to Google or other scams promoting VPN apps, browser extensions, or affiliate sites.
This phishing scam is widely spread, with BleepingComputer seeing numerous posts created each day by friends and family who unwittingly had their accounts hacked through the same scam.
As this phishing attack does not attempt to steal two-factor authentication (2FA) tokens, it is strongly advised that Facebook users enable 2FA to prevent their accounts from being accessed if they fall for a phishing scam.
Once enabled, Facebook will prompt you to enter a unique one-time passcode each time your credentials are used to log in to the site from an unknown location. As only you will have access to these codes, even if your credentials are stolen, they cannot log in.
For the best security, when enabling two-factor authentication on Facebook, use an authentication app rather than SMS texts, as your phone number can be stolen in SIM swapping attacks.
Update 1/21/24: Article updated to clarify this phishing campaign started a year ago.



