- January 30, 2024
- 04:28 PM
- 1

The U.S. Department of Justice arrested and charged two more suspects for their involvement in the hacking of almost 68,000 DraftKings accounts in a November 2022 credential stuffing attack.
One month later, DraftKings said it had refunded hundreds of thousands of dollars stolen from 67,995 customers whose accounts were hijacked in the incident.
A third defendant, Joseph Garrison, was charged in May 2023 for his involvement in the same scheme targeting the fantasy sports and sports betting website. In November, he also pled guilty to conspiring to commit computer intrusion in connection with this attack and will be sentenced on Thursday.
Credential stuffing attacks use automated tools to make millions of login attempts using a list of user/password pairs. This technique is particularly effective against accounts where the owner has reused the same login information across multiple platforms.
According to the complaint, Nathan Austad (aka Snoopy) and Garrison used a list of credentials collected from other breaches to hack into the DraftKings accounts and then sold access to the accounts to others who stole around $635,000 from roughly 1,600 compromised accounts.
While Austad and Garrison sold some of the hacked accounts using their own "shops," they also sold many of them in bulk to Kamerin Stokes (aka TheMFNPlug).
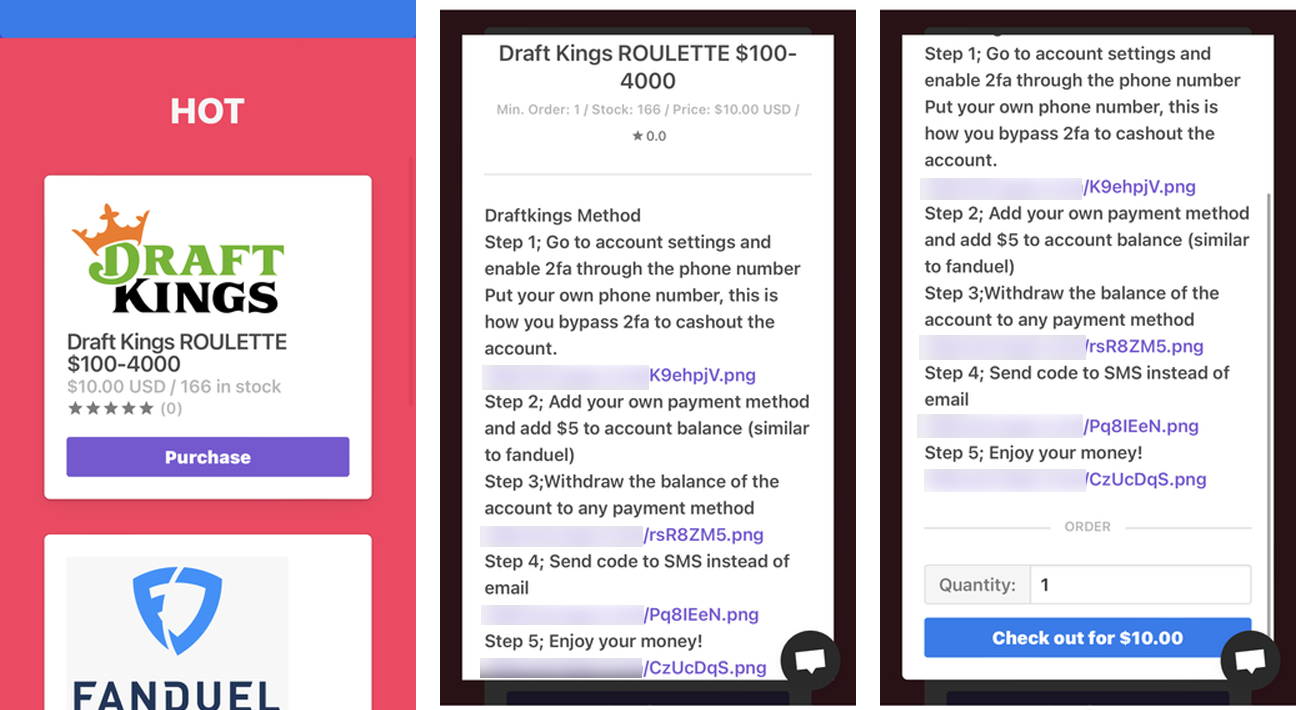
Together, the defendants also devised a method allowing buyers of the stolen DraftKings accounts to withdraw all available funds.
They instructed their "customers" to add a new payment method to the compromised accounts, deposit $5 through the newly added payment method to verify its validity, and then withdraw all existing funds to a separate financial account under their control.
While analyzing Austad's seized phone, law enforcement agents found more evidence implicating him in the DraftKings credential attack, including discussions with coconspirators regarding the hack.
They also found hundreds of "configs" used by credential-stuffing attack tools (e.g., OpenBullet and SilverBullet) on devices seized from Austad and Garrison, as well as dozens of wordlists containing tens of millions of username and password combinations also used for credential stuffing.
During the same period in November, FanDuel customers reported account compromises after credential-stuffing attacks, with stolen accounts sold on cybercrime marketplaces for as little as $2.
According to court documents, Garrison ran the "Goat Shop" website, selling hijacked DraftKings and FanDuel accounts, making $2,135,150.09 after pushing 225,247 'products.'
Chick-fil-A also confirmed in March 2023 (following an investigation started last January) that 71,473 customers had their accounts breached following a months-long credential stuffing attack that targeted the platform between December 18th, 2022, and February 12th, 2023.
Garrison's Goat Shop was also selling stolen Chic-Fil-A accounts at the time, providing instructions on how buyers could use the stored rewards points.
Automated tools and aggregated stolen credentials fuel a massive surge of credential stuffing attacks, as the FBI warned almost two years ago.



