- February 10, 2024
- 10:11 AM
- 0

Recent versions of the Raspberry Robin malware are stealthier and implement one-day exploits that are deployed only on systems that are susceptible to them.
One-day exploits refer to code that leverages a vulnerability that the developer of the impacted software patched recently but the fix has either not been deployed to all clients or it has not been applied on all vulnerable systems.
From the moment the vendor discloses the vulnerability, which usually comes with publishing a patch, threat actors rush to create an exploit and use it before the fix propagates to a large number of systems.
According to a report from Check Point, Raspberry Robin has recently used at least two exploits for 1-day flaws, which indicates that the malware operator either has the capability to develop the code or has sources that provide it.
Raspberry Robin background
Raspberry Robin is a worm that Red Canary, a managed detection and response company, first identified in 2021. It spreads primarily through removable storage devices such as USB drives to establish a foothold on infected systems and facilitate the deployment of additional payloads.
It has been associated with threat actors like EvilCorp, FIN11, TA505, the Clop ransomware gang, and other malware operations, but its creators and maintainers are unknown.
Since its discovery, Raspberry Robin has continuously evolved, adding new features, evasion techniques, and adopting several distribution methods. One example of evasion trick it implemented was to drop fake payloads to mislead researchers.
Check Point reports that it has observed an uptick in Raspberry Robin's operations starting October 2023, with large attack waves targeting systems worldwide.
A notable switch in recent campaigns is the use of the Discord platform to drop malicious archive files onto the target, likely after emailing the links to the target.
The archives contain a digitally signed executable (OleView.exe) and a malicious DLL file (aclui.dll) that is side-loaded when the victim runs the executable, thus activating Raspberry Robin in the system.
Targeting n-day flaws
When Raspberry Robin is first run on a computer, it will automatically attempt to elevate privileges on the device using a variety of 1-day exploits.
Check Point highlights that the new Raspberry Robin campaign leverages exploits for CVE-2023-36802, and CVE-2023-29360, two local privilege escalation vulnerabilities in Microsoft Streaming Service Proxy and the Windows TPM Device Driver.
In both cases, the researchers say, Raspberry Robin started exploiting the flaws using a then-unknown exploit less than a month after the security issues were disclosed publicly, on June 13 and September 12, 2023.
As illustrated in the timeline diagram below, Raspberry Robin exploited the two flaws before security researchers first published proof of concept exploit code for the two flaws.

Specifically, regarding CVE-2023-36802, which enables attackers to escalate their privileges to the SYSTEM level, Cyfirma reported that an exploit had been available for purchase on the Dark Web since February 2023, a full seven months before Microsoft acknowledged and addressed the issue.
This timeline suggests that Raspberry Robin acquires 1-day exploits from external sources almost immediately after their disclosure, as their cost as zero days is likely too much even for larger cybercrime operations.
Check Point found evidence that points to this theory as well, since the exploits used by Raspberry Robin were not embedded into the main 32-bit component, but deployed as external 64-bit executables, and also lack the heavy obfuscation typically seen with this malware.
New evasion mechanisms
Check Point's report also highlights several advancements in the latest Raspberry Robin variants, which include new anti-analysis, evasion, and lateral movement mechanisms.
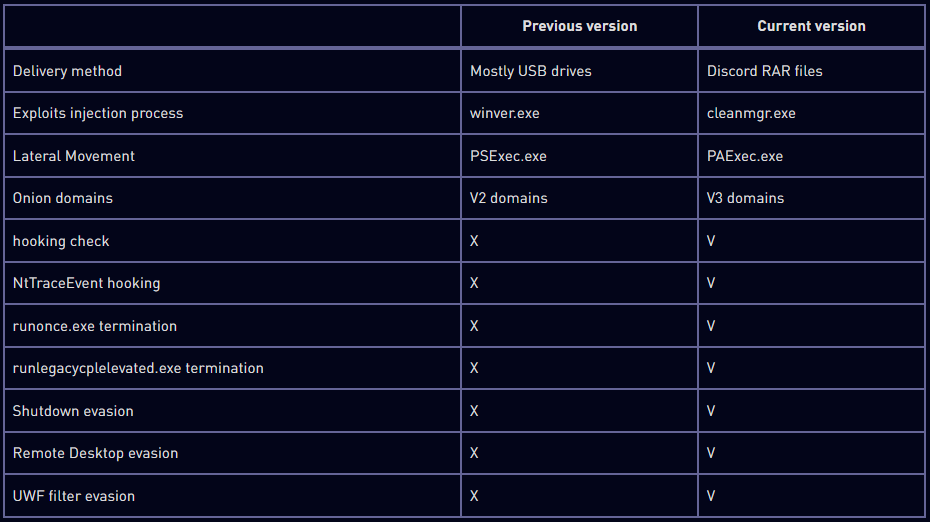
To evade security tools and OS defenses, the malware now attempts to terminate specific processes like 'runlegacycplelevated.exe,' related to Use Account Control (UAC), and patches the NtTraceEvent API to evade detection by Event Tracing for Windows (ETW).
Moreover, Raspberry Robin now checks if certain APIs, like 'GetUserDefaultLangID' and 'GetModuleHandleW', are hooked by comparing the first byte of the API function to detect any monitoring processes by security products.
Another interesting new tactic is the implementation of routines that use APIs like 'AbortSystemShutdownW' and 'ShutdownBlockReasonCreate' to prevent system shutdowns that could interrupt the malware's activity.
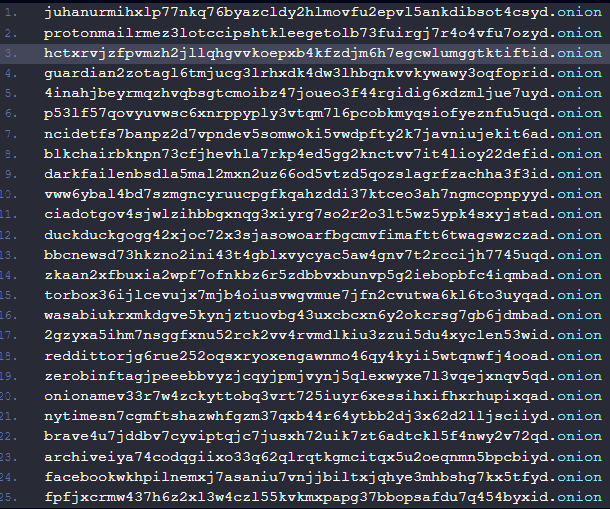
To conceal the command and control (C2) addresses, the malware first randomly engages with one of the 60 hard-coded Tor domains pointing to well-known sites to make initial communications appear benign.
Finally, Raspberry Robin now uses PAExec.exe instead of PsExec.exe to download the payload directly from the hosting location. This decision was likely made to increase its stealth, as PsExec.exe is known to be misused by hackers.
The researchers believe that Raspberry Robin will keep evolving and add new exploits to its arsenal, seeking code that has not been released publicly. Based on observations during the malware analysis, it is likely that the operators of the malware does not create is connected to a developer that provides the exploit code.
Check Point's report provides a list of indicators of compromise for Raspberry Robin, which consists in hashes for the malware, multiple domains in the Tor network, and Discord URLs for downloading the malicious archive.



