- April 4, 2024
- 10:01 AM
- 0
Among the never-ending list of malicious software that threat actors use in cyber attacks are viruses, worms, trojans, ransomware, spyware, and adware. Today's malware is not just about causing immediate damage; some programs get embedded within systems to siphon off data over time, disrupt operations strategically, or lay the groundwork for massive, coordinated attacks.
A prime example is a recently found malicious backdoor in a popular compression tool, known as xz Utils. Thankfully the malicious code was identified early “due to bad actor sloppiness”, but the consequences could’ve been massive.
Read on to get the lowdown on recent high-profile malware attacks along with strategies to help limit malware risks at your organization.
Recent High-Profile Malware Attacks
Here's a detailed overview of recent malware attacks, highlighting key incidents and offering valuable insights and lessons learned from each event.
StripedFly
A prolific and advanced cross-platform malware framework infected over a million Windows and Linux systems during a five-year spell. Researchers only uncovered StripedFly in 2022, and its stealthy capabilities included a built-in TOR network tunnel.
Takeaways:
-
Malware continues to get more complex; this malicious framework comes with several modules that aid with the evasion of security tools, establishing persistence with PowerShell scripts, and more.
-
Persistent and stealthy operations are central to modern malware, which increases the need for advanced and layered security strategies.
Banking Trojans
In 2023, ten new Android banking trojans emerged that targeted 985 bank and fintech/trading apps. Opportunistic cybercriminals use these trojans, often disguised as legitimate apps, to trick people into downloading them. In the background, they intercept and manipulate banking sessions, capture login credentials, and even bypass multi-factor authentication methods.
Takeaways:
-
10 new Android banking trojans in a single year highlight the prominent trend of malware targeting financial apps.
-
Banking trojans are getting more advanced, with 2024’s versions having features like automated transfer systems and live screen-sharing.
Dutch Ministry of Defense
News emerged in early 2024 that Chinese hackers managed to infiltrate the Dutch Ministry of Defence’s network with malware in 2023. The threat actors used sophisticated malware called "Coathanger."
This malware was notable for its ability to persist through firmware upgrades and system reboots, which made it particularly difficult to detect and remove.
Takeaways:
-
This attack underscores the strategic use of advanced malware in state-sponsored cyber operations.
-
More advanced malware is increasingly resilient and persistent, which shows the need for advanced threat detection and response.
How You Can Limit Malware Risks
With 5.5 billion worldwide malware attacks each year, this is one cyber threat that pretty much every business needs to think about and limit its exposure to. Here are five must-have strategies for effective malware risk reduction.
Anti-virus, Anti-malware Software
Anti-virus and anti-malware solutions are cornerstone elements in malware risk reduction. The use of both types of solutions addresses the broad spectrum of malware threats that your organization will face.
Anti-virus software prevents, detects, and removes viruses and worms. These tools mostly use signature-based detection, which involves scanning files and comparing them to a database of known virus signatures. Modern anti-virus solutions also include heuristic analysis that enables them to detect novel computer viruses by analyzing behaviors and characteristics common to malicious software.
Anti-malware tools combat a wider range of malicious software, including newer and more sophisticated threats like ransomware, spyware, and zero-day attacks (threats that exploit previously unknown vulnerabilities).
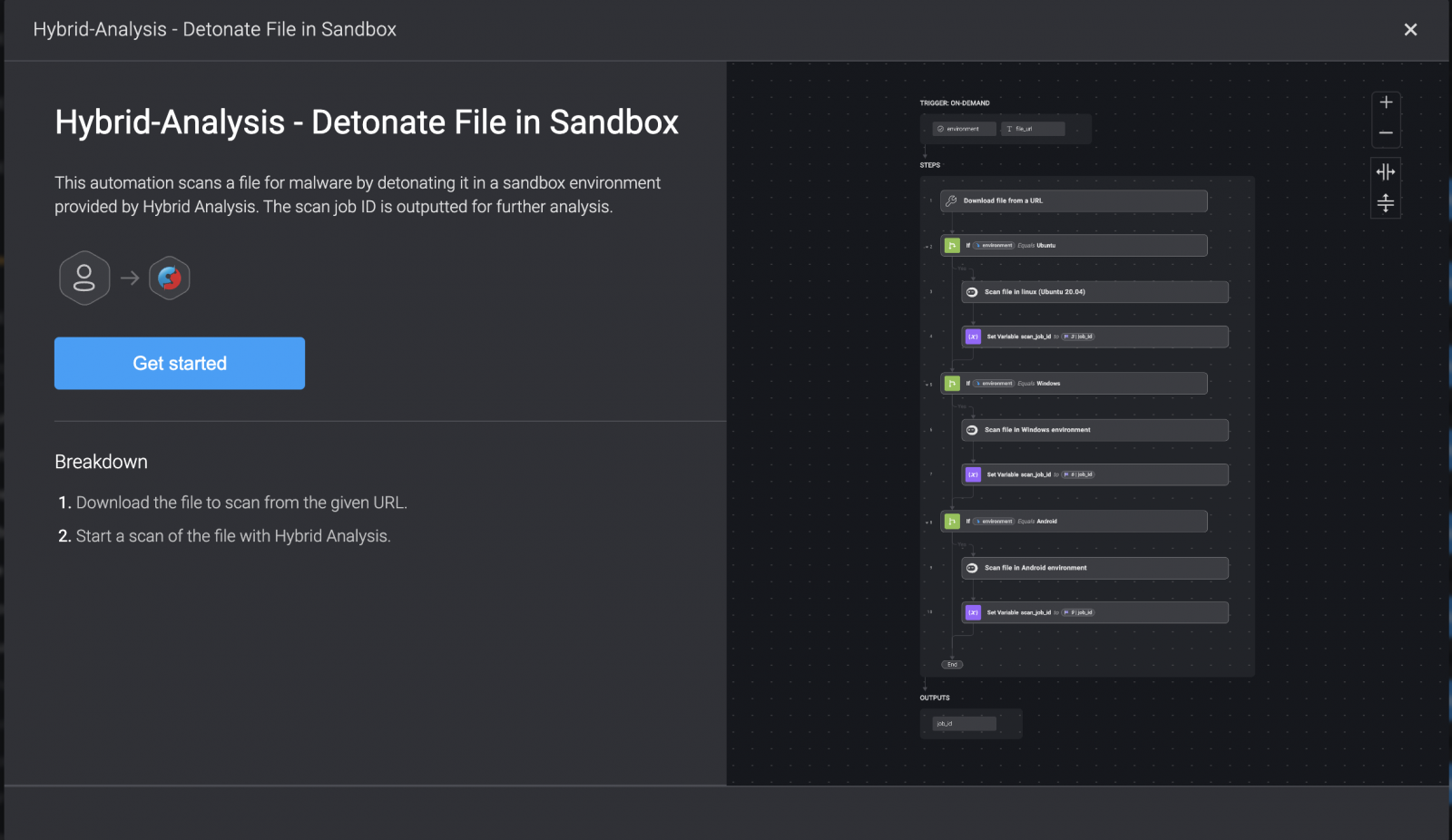
Alongside signature-based detection, these solutions also use machine learning and behavioral analysis. It’s easy to automate tasks related to your anti-malware software using a security automation copilot.
For instance, Blink can automatically scan a file for malware by detonating it in a sandbox environment provided by Hybrid Analysis.
Regular Employee Training
While traditional technical safeguards like anti-virus and anti-malware are important, don’t underestimate the role of human awareness and intuition.
Regular training makes employees more capable of spotting signs of the latest malware trends and tactics, such as specific phishing campaigns or malicious attachments in team collaboration tools.
Web browsing is one of the main access vectors for malware. Security training also emphasizes the importance of cautious online behavior like not downloading things from untrusted websites or not clicking dodgy links.
Device Management
Device management is all about securely deploying, monitoring, and maintaining devices connected to your network to prevent unauthorized access and protect against malware.
This includes IT admins enforcing security policies across user devices and automating software updates to close off vulnerabilities before hackers exploit them to install malware.
Another important part of device management is controlling which applications your users can install on workstations. Consider whitelisting approved apps and blocking unauthorized software installations.
Some enterprise device management tools can remotely wipe sensitive data or lock systems in the event a computer, laptop, or USB drive gets lost or stolen.
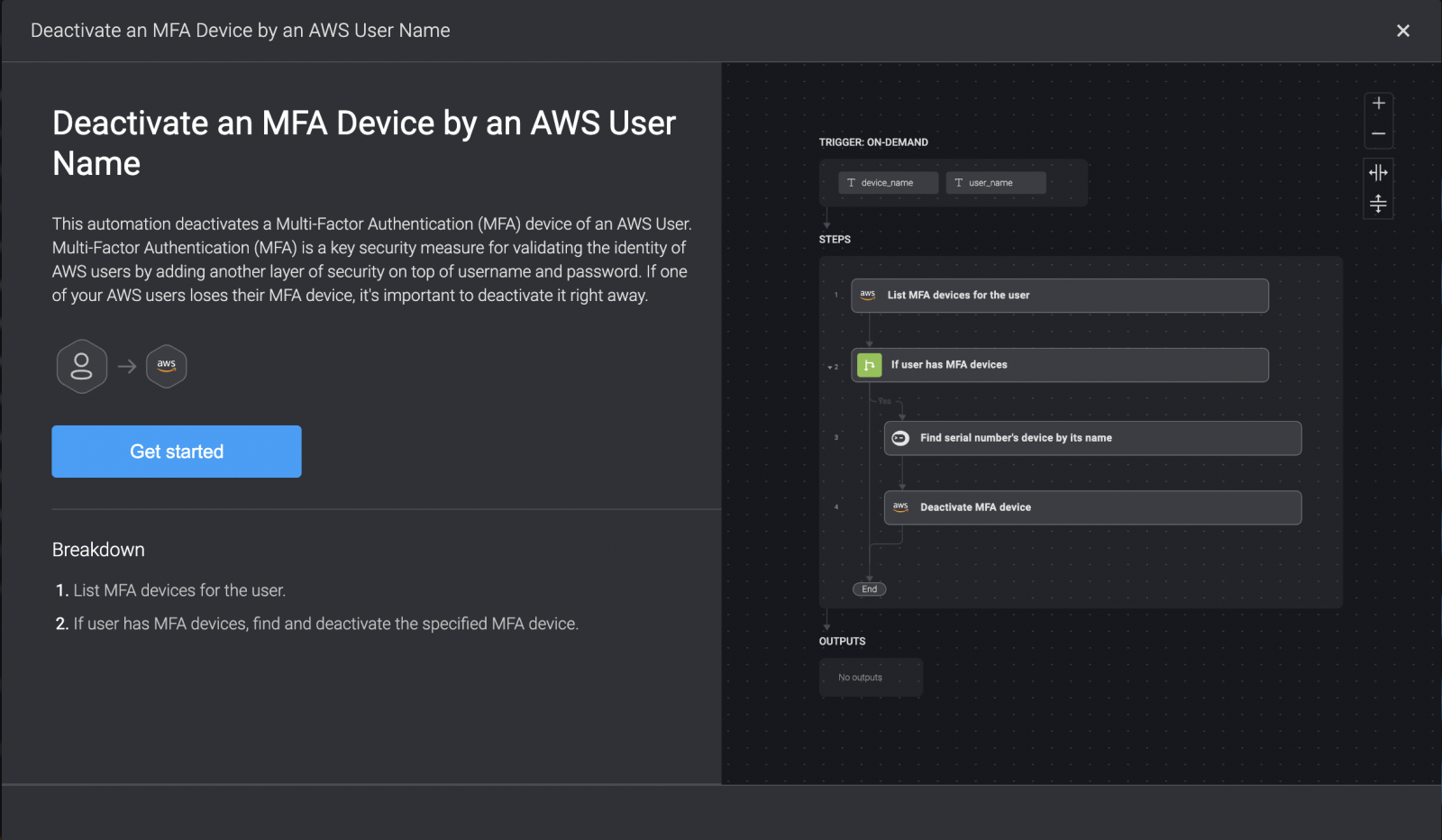
Automating device management tasks can boost efficiency for your IT team. For instance, you could use the automation below, which quickly deactivates a missing or stolen MFA device of an AWS user.
User Behavior Analysis
Training employees is great, but it’s still helpful to know what they’re doing and what apps/websites they’re interacting with.
After all, mistakes still happen, and sophisticated threat actors might still be able to install malware on devices. User Behavior Analysis (UBA) deploys machine learning and data analytics to get a detailed understanding of user activity within your organization's network.
This analysis helps better identify anomalies that could indicate a malware infection.
The technical prowess of UBA lies in its ability to detect subtle, yet potentially malicious, activities that could elude traditional security tools.
Anomalies like a user accessing high volumes of data at strange times or data transfers to external drives/services could indicate the presence of a trojan horse that has hijacked that user's credentials to exfiltrate data.
User Privilege Management
When users have more access privileges than they need, this creates a larger attack surface for malware to infect and spread within your network. An interesting survey of IT pros in the US found that 45 percent believed users in their company have more access privileges than they need.
User privilege management addresses this through things like role-based access controls, regular privilege audits and reviews, multi-factor authentication (MFA), and automated de-provisioning of access to resources when people leave or change roles.
How Automation Helps Reduce Malware Risks
Automation is a powerful tool in the malware defense arsenal. After identifying a threat, automated systems or security workflows can execute predefined response actions, such as isolating infected devices, detonating files in sandboxes, or blocking malicious communication without the need for manual intervention.
This automation speeds up the response to attacks and minimizes the potential damage malware can cause.
Threats extend beyond just malware. Schedule a demo of Blink today to discover everything you can automate.



