- April 9, 2024
- 09:00 AM
- 0

Researchers have discovered two techniques that could enable attackers to bypass audit logs or generate less severe entries when downloading files from SharePoint.
Microsoft SharePoint is a web-based collaborative platform that integrates with Microsoft Office and 365, primarily as a document management and data storage system.
Many companies use it for document management and collaboration, creating websites and corporate intranets, automating complex workflows, and enterprise content management applications.
Due to the sensitivity of SharePoint data, many companies audit sensitive events, like the downloading of data, to trigger alerts in cloud access security tools, data loss prevention tools, and security information and event management platforms (SIEMs).
Source: Varonis
Researchers at the Varonis Threat Labs have devised two simple techniques that enable users to bypass audit logs or generate less sensitive events by downloading data a certain way or disguising it as data syncing actions.
Silent data exfiltration
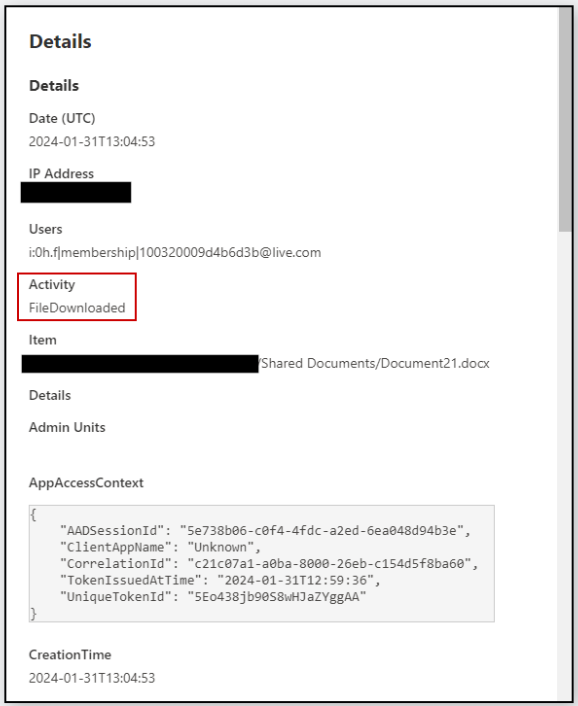
The first technique described in Varonis' report takes advantage of SharePoint's "Open in App" feature, which allows users to open documents with applications like Microsoft Word instead of using the web browser, which is the default option.
Utilizing this feature does not generate a "FileDownloaded" event in SharePoint's audit logs but instead creates an "Access" event that administrators may ignore.
Source: Varonis
Opening the file from a cloud location creates a shell command with the non-expiring URL from the file's location on the cloud endpoint, which someone can use to download the file without restrictions.
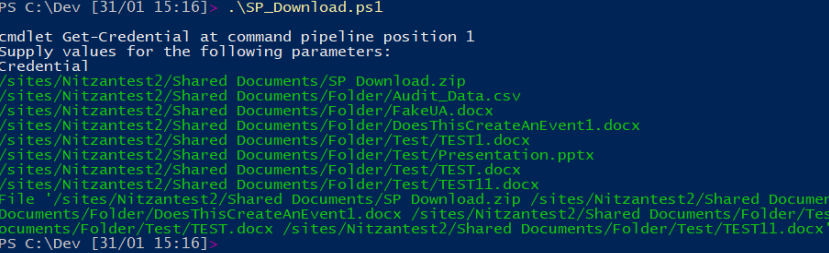
Varonis also notes that misuse of "Open in App" can be both manual and automated, using a custom PowerShell script that could enable someone to exfiltrate large lists of files quickly.
Source: Varonis
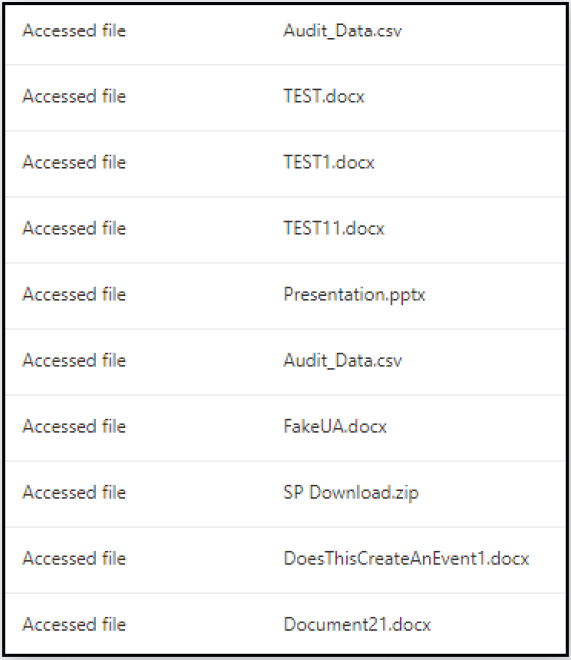
The second technique involves spoofing the User-Agent string of the file access requests to mimic Microsoft SkyDriveSync, a service used for file synchronization between SharePoint and a user's local computer.
This trick makes the file downloads performed via the browser or Microsoft Graph API appear in the logs as data syncing events ("FileSyncDownloadedFull"), reducing the likelihood of scrutiny by security teams.
In this case, too, the alteration of the User-Agent string and subsequent file exfiltration can be done manually or via a PowerShell script to automate the process.
Mitigation
Varonis disclosed these bugs in November 2023, and Microsoft added the flaws to a patch backlog for future fixing.
However, the issues were rated as moderate severity, so they won't receive immediate fixes. Therefore, SharePoint admins should be aware of these risks and learn to identify and mitigate them until patches become available.
Varonis recommends monitoring for high volumes of access activity within a short timeframe and the introduction of new devices from unusual locations, which could be signs of unauthorized data exfiltration.
Moreover, security teams are recommended to scrutinize sync events for anomalies in frequency and data volumes and try to identify unusual activity patterns.
BleepingComputer has reached out to Microsoft to learn more about their plans for addressing the issues presented by Varonis, but we have yet to receive a comment.



