- April 11, 2024
- 10:16 AM
- 2

Apple has been notifying iPhone users in 92 countries about a "mercenary spyware attack" attempting to remotely compromise their device.
In a sample notification the company shared with BleepingComputer, Apple says that it has high confidence in the warning and urges the recipient to take seriously.
"Apple detected that you are being targeted by a mercenary spyware attack that is trying to remotely compromise the iPhone associated with your Apple ID -xxx-," reads the notification.
To protect against such attacks, Apple recommends a set of immediate actions that include enabling lockdown mode on the device, updating the iPhone and any other Apple products to the latest software version, and seeking expert assistance such as that from the Digital Security Helpline - a non-profit that provides technical support at no cost for journalists, activists, and human rights defenders.
When describing mercenary spyware attacks, the notification highlights NSO Group’s Pegasus kit and says that they are exceptionally well-funded, sophisticated, and target a very small number of individuals.
Apple also updated its support page on spyware protection yesterday replacing the term “state-sponsored” with “mercenary spyware,” noting that these attacks are ongoing and global and sometimes involve private companies that develop spying tools for state actors.
Primary targets of these attacks typically include journalists, activists, politicians, and diplomats due to their roles or the sensitive information they may possess.
Despite the sophistication of these attacks, Apple assures users it’s doing everything in its power to detect them, alert users, and assist them in taking the necessary action.
“Mercenary spyware attacks cost millions of dollars and often have a short shelf life, making them much harder to detect and prevent,” reads the updated support page.
“Since 2021, we have sent Apple threat notifications multiple times a year as we have detected these attacks, and to date, we have notified users in over 150 countries in total,” Apple informs.
BleepingComputer asked Apple to comment on the targeting scope of the latest campaign it detected, but a spokesperson declined to provide clarifications.
On a related note, in the updated support page, Apple says that the “extreme cost, sophistication, and worldwide nature of mercenary spyware attacks makes them some of the most advanced digital threats in existence today.
Because of this, the company does not attribute the attacks to a specific attacker or or geographical regions.
What to do if targeted
If you’re targeted by mercenary spyware attacks, you will get an email and iMessage notification at the numbers registered with your Apple ID, while a threat notification will also be displayed on the Apple ID portal after login, as a way to confirm authenticity.
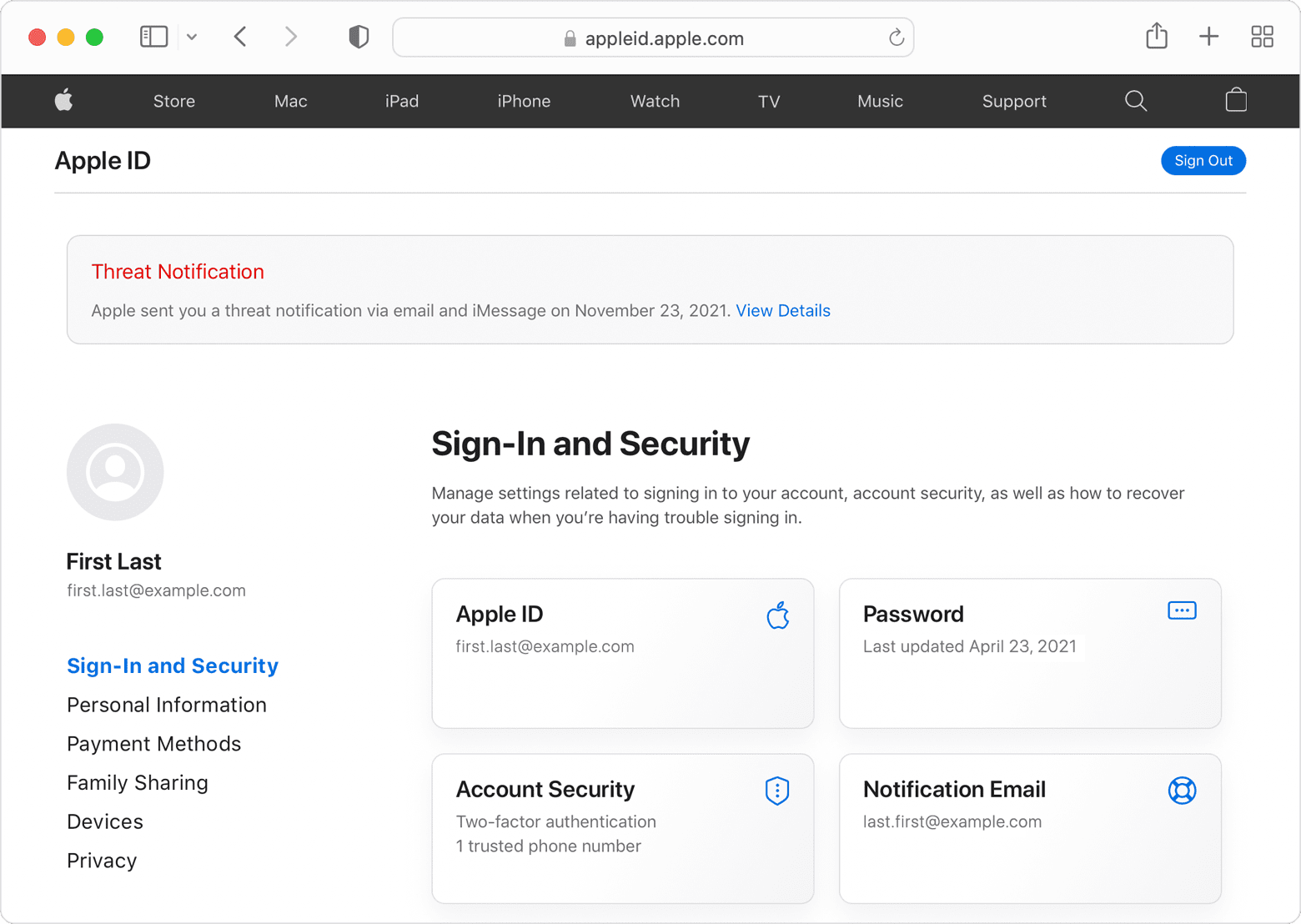
The actions Apple recommends that people take in that case are the following:
- Contact the Digital Security Helpline at Access Now for emergency security help and advice.
- Turn on Lockdown Mode for added protection against spyware, significantly reducing the attack surface.
- Update messaging and cloud apps to the latest available versions.
- Update all other Apple devices (Mac, iPad) you use and enable Lockdown Mode on those too.
- Follow general good practices like applying the latest updates, using passcodes, enabling two-factor authentication, downloading apps only from the App Store, using strong and unique passwords, and avoiding opening suspicious links or attachments.
Apple cannot detect all spyware attacks, so if you suspect you’re being targeted, it’s advisable to enable Lockdown Mode even if you have received no notifications from the company.



