- February 22, 2024
- 08:51 AM
- 0

LockBit ransomware developers were secretly building a new version of their file encrypting malware, dubbed LockBit-NG-Dev - likely to become LockBit 4.0, when law enforcement took down the cybercriminal's infrastructure earlier this week.
As a result of the collaboration with the National Crime Agency in the UK, cybersecurity company Trend Micro analyzed a sample of the latest LockBit development that can work on multiple operating systems.
LockBit next-gen
While previous LockBit malware is built in C/C++, the latest sample is a work-in-progress written in .NET that appears to be compiled with CoreRT, and packed with MPRESS.
Trend Micro says that the malware includes a configuration file in JSON format that outlines the execution parameters such as execution date range, ransom note details, unique IDs, RSA public key, and other operational flags.
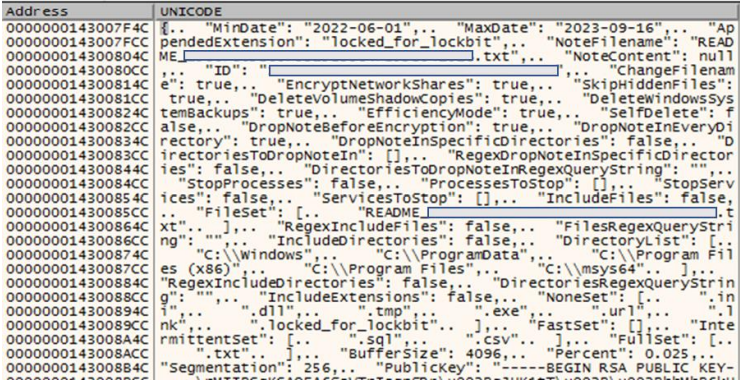
Although the security firm says the new encryptor lacks some features present in previous iterations (e.g. ability to self-propagate on breached networks, printing ransom notes on victim's printers), it appears to be in its final development stages, already offering most of the expected functionality.
It supports three encryption modes (using AES+RSA), namely "fast," "intermittent," and "full," has custom file or directory exclusion, and can randomize the file naming to complicate restoration efforts.
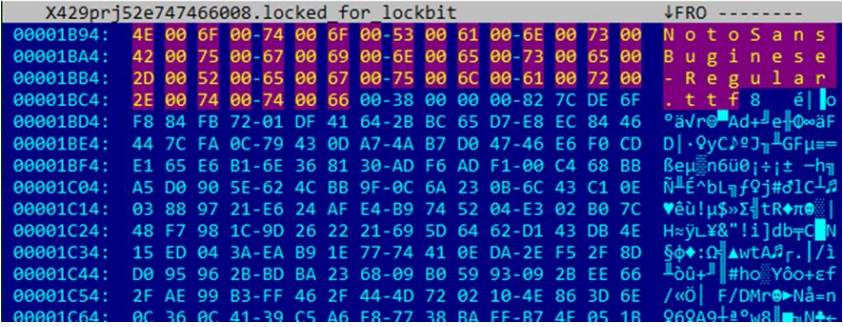
Additional options include a self-delete mechanism that overwrites LockBit's own file contents with null bytes.
Trend Micro has published a deeply technical analysis of the malware, which reveals the full configuration parameters for LockBit-NG-Dev.
The discovery of the new LockBit encrypter is another blow law enforcement dealt to LockBit operators through Operation Cronos. Even if backup servers are still controlled by the gang, restoring the cybercriminal business should be a tough challenge when the source code for the encrypting malware is known to security researchers.



