- April 16, 2024
- 02:36 PM
- 0

Exploit code is now available for a maximum severity and actively exploited vulnerability in Palo Alto Networks' PAN-OS firewall software.
Tracked as CVE-2024-3400, this security flaw can let unauthenticated threat actors execute arbitrary code as root via command injection in low-complexity attacks on vulnerable PAN-OS 10.2, PAN-OS 11.0, and PAN-OS 11.1 firewalls if the device telemetry and GlobalProtect (gateway or portal) feature are enabled.
While Palo Alto Networks has started releasing hotfixes on Monday to secure unpatched firewalls exposed to attacks, the vulnerability has been exploited in the wild as a zero-day since March 26th to backdoor firewalls using Upstyle malware, pivot to internal networks, and steal data by a threat group believed to be state-sponsored and tracked as UTA0218..
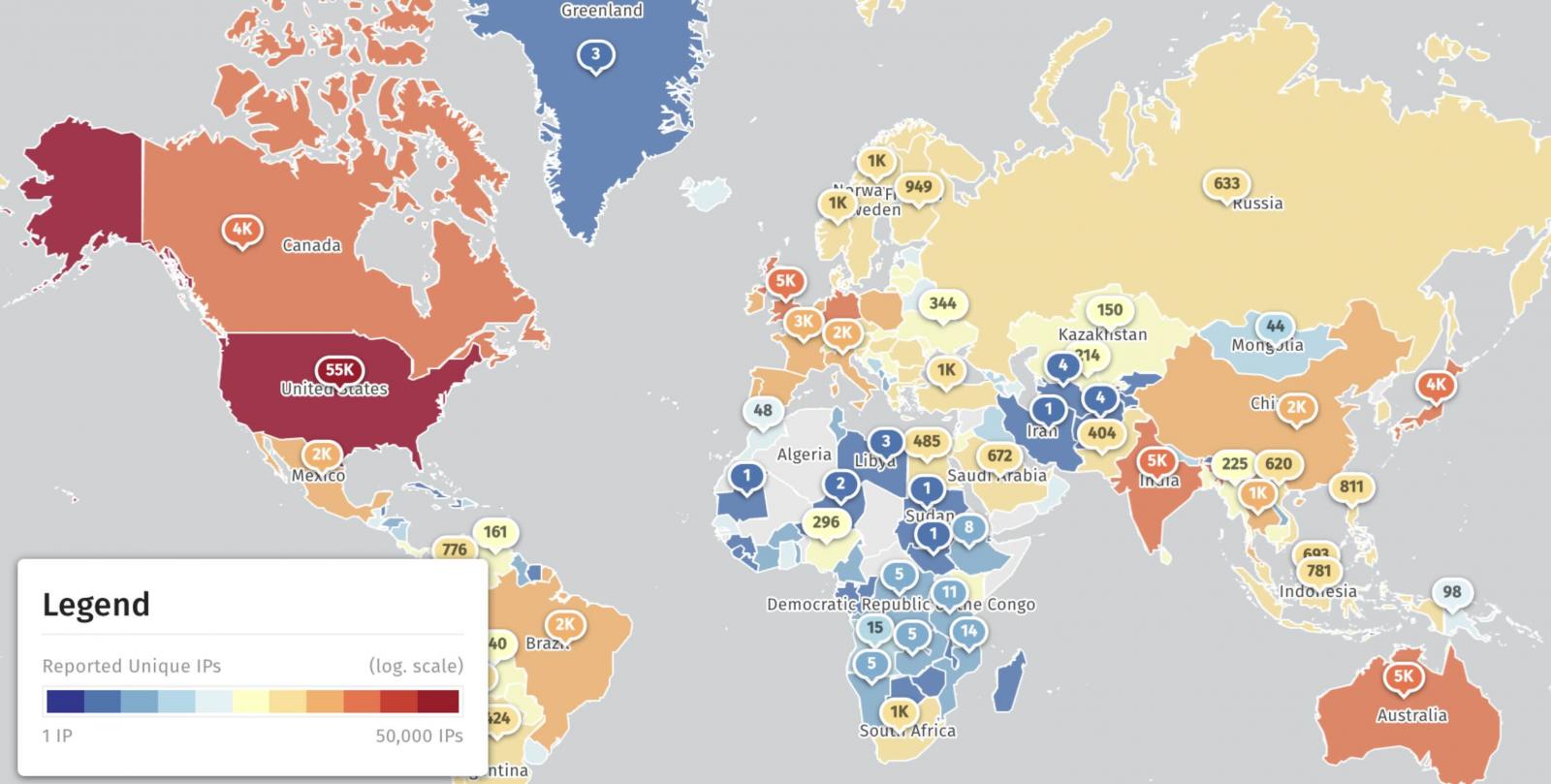
Security threat monitoring platform Shadowserver says it sees more than 156,000 PAN-OS firewall instances on the Internet daily; however, it doesn't provide information on how many are vulnerable.
On Friday, threat researcher Yutaka Sejiyama also found over 82,000 firewalls vulnerable to CVE-2024-34000 attacks, 40% of which were in the United States.
Exploit code now publicly available
One day after Palo Alto Networks started releasing CVE-2024-3400 hotfixes, watchTowr Labs also released a detailed analysis of the vulnerability and a proof-of-concept exploit that can be used to execute shell commands on unpatched firewalls.
"As we can see, we inject our command injection payload into the SESSID cookie value - which, when a Palo Alto GlobalProtect appliance has telemetry enabled - is then concatenated into a string and ultimately executed as a shell command," watchTowr Labs said.
TrustedSec Chief Technology Officer Justin Elze also shared an exploit seen in actual attacks, allowing attackers to download the firewall's configuration file.
In response to the attacks, CISA added CVE-2024-3400 to its Known Exploited Vulnerabilities (KEV) catalog on Friday, ordering U.S. federal agencies to secure their devices within seven days by April 19th.
If you're still waiting for a hotfix, disable the device telemetry feature on vulnerable devices until a patch is available.
Additionally, if you have an active 'Threat Prevention' subscription, you can block ongoing attacks by activating 'Threat ID 95187' threat prevention-based mitigation.



